Safe Email Handling Tips for Businesses
Email is a common target for malicious hackers. Two of the more common techniques they use to compromise email are business email compromise and malicious document attachments.
Business Email Compromise
The FBI describes Business Email Compromise, or BEC, as a financially-motivated and often sophisticated scam carried out by organized crime organizations. The technique involves impersonating a trusted party, then using that position of trust to convince an employee to transfer funds or sensitive data to the attacker. Some common scenarios described by the FBI’s Internet Crime Complaint Center include:
- Scammer imitates a company executive, or an actual business partner
- Requests a funds transfer, or sensitive data. Often Employee tax records (W-2 scam)
Malicious Attachments
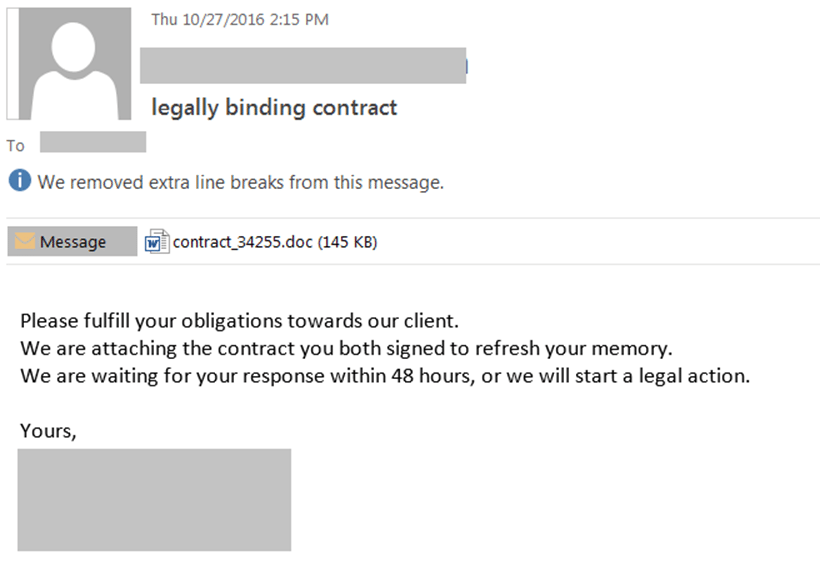
The second common technique is malicious attachments emailed to a target. These are usually less sophisticated and not tailored to a specific person, but rather the same email is copied to many different people. A recent example:
- Subject: legally binding contract
Attachment: contract_#####.doc
By default, Microsoft Office is configured to open emailed documents in Protected View – a mode that disables any malicious macros contained in the documents. If you click on the attachment, you will likely be prompted to disable Protected View so the attachment can download full-fledged malware to your PC.
Tips for Businesses to Combat these Scams
- Consider entirely blocking macros in attachments. Microsoft Office 2013 and 2016 support a GPO option to disable macros in documents that originated from the Internet (i.e. emailed or downloaded). The GPO will prevent individuals from re-enabling macros.
- Consider tagging any email originating outside the company so employees can see at a glance whether a given message is internal or external. An email from “ceo@company.com” that is marked as external should be a red flag. In some cases IT may be able to quarantine email sent from a domain that mimics the real business, but multilingual domains allow for more visually similar possibilities than most IT organizations can account for.
- Identify business processes that handle sensitive data or financial transactions, and ensure the process follows a defined, non-email authorization. For instance, perhaps the process for approving a large financial transaction involves the CFO confirming with the CEO in person or by cell phone before executing the transaction. In larger organizations it may be more appropriate to track and approve transactions through a ticketing system or the equivalent. The key point is that an email by itself is not sufficient authorization to carry out a sensitive or costly action.